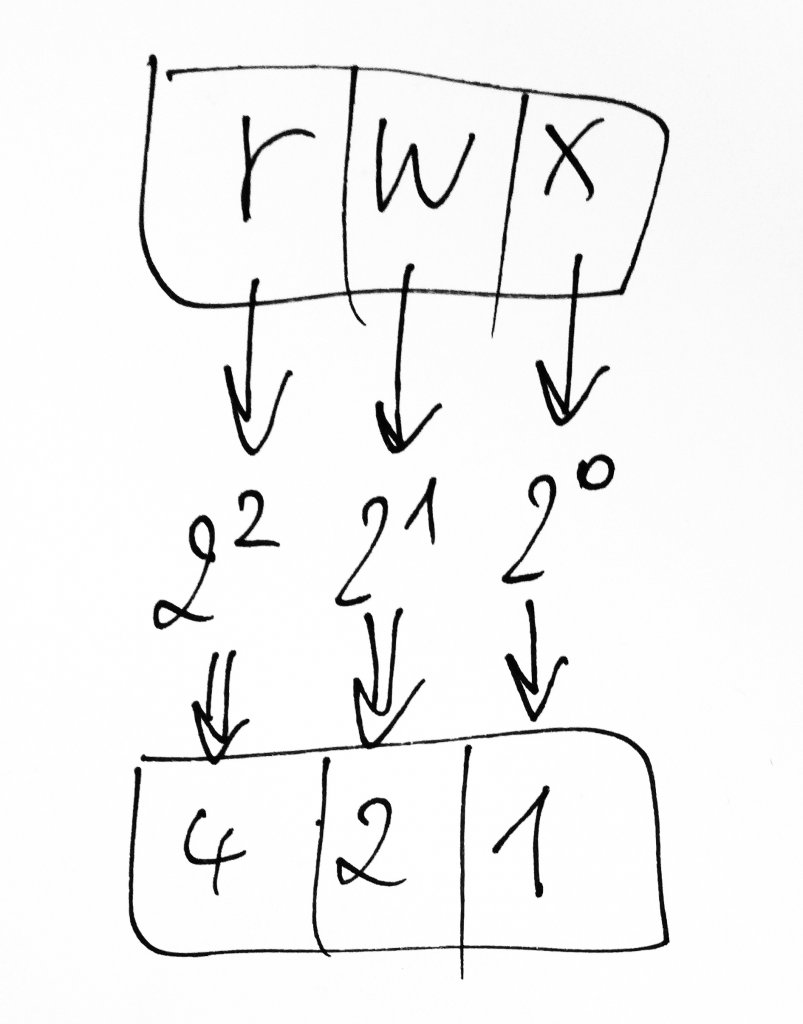
When the server can’t write to the session data directory, if will use /var/cache/nginx/fastcgi_temp/ and complain in the error log. You don’t want any of these errors, but a setting considered insecure will not even be reported as such. Here is how to bolster your PHP 7 session security with NGINX and php-fpm.