Recent revelations from the maker of networking gear Juniper Networks have shaken the industry: Juniper has identified unauthorized code in ScreenOS, its operating system that powers the NetScreen line of Juniper firewalls. Then last Friday, cryptography researchers revealed that Juniper has allowed changes to its code that could enable eavesdropping on encrypted virtual private network sessions of its customers.

All in all, not one but two separate security vulnerabilities came to light:
- an administrative access backdoor to NetScreen devices (CVE-2015-7755), and
- a separate vulnerability that could be leveraged by a “knowledgeable attacker” (using a valid user password) allowing them to monitor VPN traffic and decrypt VPN connections (CVE-2015-7756).
The administrative access backdoor “only” impacts ScreenOS 6.3.0r17 through 6.3.0r20. How “cool” is that.
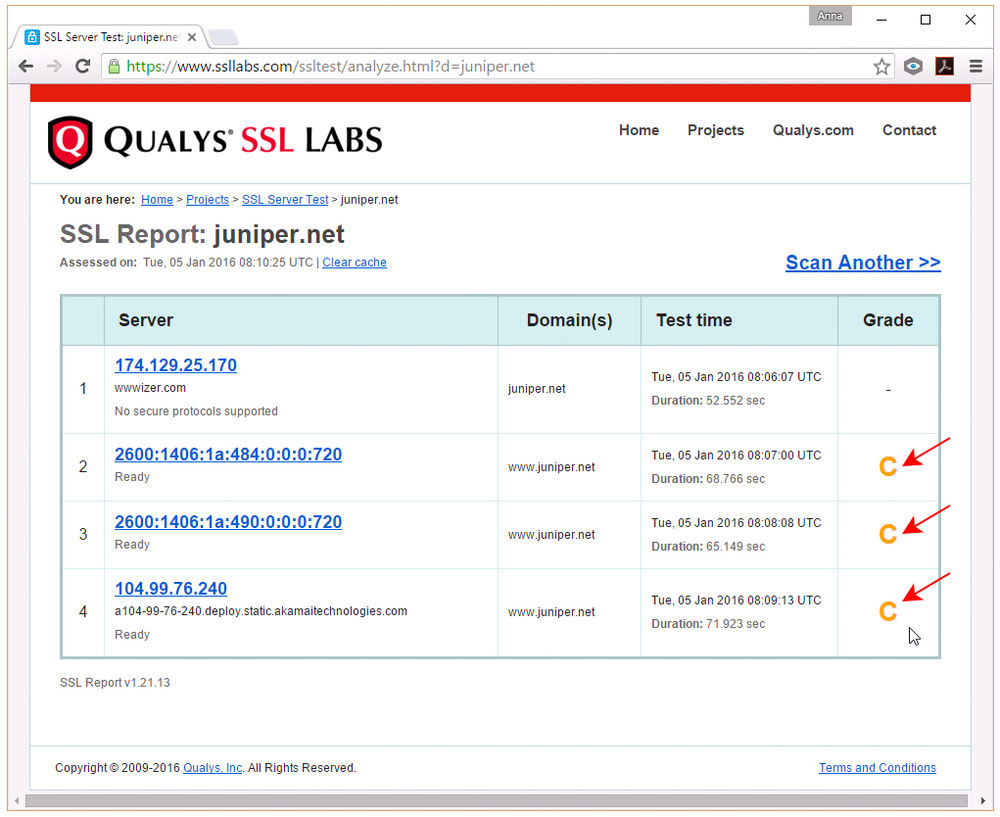
Realizing the potential for lasting damage to its otherwise rather flawless reputation, Juniper has hurriedly patched ScreenOS with the release of versions 6.2.0r19 and 6.3.0r21 (also 6.3.0r12b, 6.3.0r13b, 6.3.0r14b, 6.3.0r15b, 6.3.0r16b, 6.3.0r17b, 6.3.0r18b and 6.3.0r19b), but forgot to patch its own flawed SSL configuration (see below).
The authentication backdoor could be exploited via SSH or Telnet using a default password that is set on every affected device, but why would you want to allow Telnet connections to a firewall in the first place?
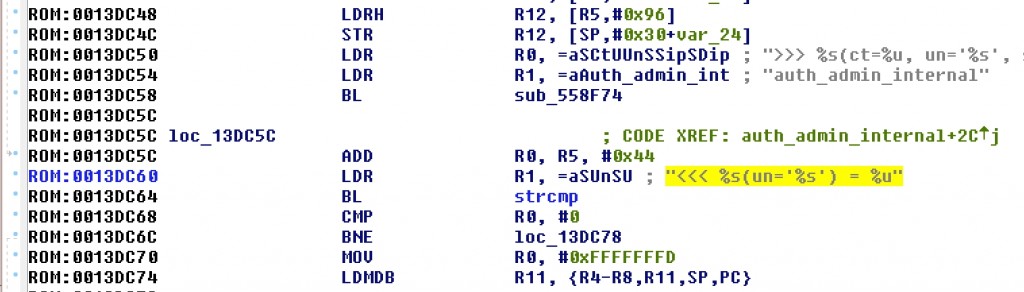
The inconspicuously looking password has been hidden in the ScreenOS code for years and was able to remain undetected due to its sheer brilliance (makes you wonder who signed off on the code without as much as reading it):
<<< %s(un='%s') = %u
According to Juniper, the password could “only” be leveraged by an attacker who knew a valid username for the device. Go figure.
The roots of Juniper’s embarrassment run deeper than incompetence. In a public announcement this past Friday, Juniper Networks Inc said that it would stop using a piece of security code that analysts believe was developed by the National Security Agency in order to eavesdrop on the users of technology products. During a presentation at Stanford University, a team of cryptographers revealed that Juniper’s code had been changed in multiple ways during 2008 to enable eavesdropping on encrypted VPN sessions.
Juniper, for its part, has admitted to code changes going back to 2012 and 2014. According to Hovav Shacham, a security researcher of the University of California, San Diego, the 2014 backdoor was straightforward, allowing anyone with the right password access to everything. In 2012, Juniper changed a mathematical constant in Dual Elliptic Curve (Dual EC) used in its Netscreen products that should have enabled its author to eavesdrop on supposedly “encrypted” communications. In its original patch, Juniper hurriedly reversed the constant to the version that had been in use after the 2008 changes, but failed to explain why it was relying on a faulty algorithm to begin with.
Dual Elliptic Curve cryptography is being used most prominently by RSA, a member company in the EMC Federation, which according to Reuters was granted a $10 million federal contract to distribute it in a software kit to be used by others. (EMC is currently in the process of being acquired by Dell, Inc.).
In the meantime, Fortinet, another maker of network security gear, landed in hot water when a hard-coded password backdoor to its FortiGate firewalls was publicly revealed (“FGTAbc11*xy+Qqz27”, you’re welcome). At least Fortinet has discovered the issue and quietly patched the vulnerability back in July 2014 (CVE-2014-2216) in version 5.2.3 without releasing a security advisory at the time. A security advisory calling on customers to perform upgrades has been only released recently in response to the public outcry over the hard-coded password vulnerability.
We are safe… We are protected by 2 layers of firewalls: Juniper & Fortigate! #backdoors #infosechumor
— Xavier Mertens (@xme) January 13, 2016

Leave a Reply